Computer chatter 1: Networks and data transmission
About this lesson
In this lesson sequence students relate the concept of transportation systems to help them develop an understanding of the properties of networked systems and the underlying techniques used to transmit and validate data.
Year band: 7-8
Curriculum Links AssessmentCurriculum Links
Links with Digital Technologies Curriculum Area
| Strand | Content Description |
|---|---|
| Knowledge and Understanding |
Investigate how data is transmitted and secured in wired and wireless networks including the internet (AC9TDI8K02). |
| Processes and Production Skills |
acquire, store and validate data from a range of sources using software, including spreadsheets and databases (AC9TDI8P01). |
Assessment
Below are some learning sequence specific examples of formative and summative assessment.
Formative assessment
The structure of the activities provides ample opportunities for formative assessment while the learning takes place. The list below identifies the various stages in the activities where student progress can be evaluated. Note that this does not need to be a formal process, but feedback to students is always encouraged and these opportunities naturally occur in the lesson sequence:
- student responses to teacher prompts
- think-pair-share and discussion
- PMI and other reflection activities
- participation and engagement in the physical activities
- one-on-one support through the research activity
- peer collaboration
- debating alternative views and perspectives on controversial issues.
Where students struggle to articulate their progress towards the learning goals, consider intervention strategies that will support the students to overcome sticking points, or to address any skill or knowledge gaps the student may have.
Summative assessment rubric
Present summative assessment rubrics that are tailored to meet the specific learning goals identified for any assessment item. These should be explicit, identify the specific knowledge, understanding and skills that should be demonstrated, and use measurable outcomes and language that students can understand.
The rubric below is not meant to be used as a task rubric. It has been produced to assist you to determine the appropriate level of knowledge and understanding of the key concepts presented in the activities for student achievement at each year level. This should be used alongside the Australian Curriculum achievement standards and any school or jurisdiction guidelines for summative assessment purposes.
Think of the depth of knowledge and understanding as being a continuum. Students who are operating at a relational level, for example, will also be able to demonstrate the multi-structural knowledge acquisition presented.
| Quantity of knowledge | Quality of understanding | ||||
|---|---|---|---|---|---|
| Criteria | Pre-structural | Uni-structural | Multi-structural | Relational | Extended abstract |
| Structure and types of networks | Can identify some of the key features of a network, but is unclear on their roles in the system or how data moves between them | Understands the route data travels between main components of a network but does not fully understand the purpose of each step; can state different types of networks | Can identify important parts of a network and distinguish between them; explains simple reasons for choosing one type of infrastructure over another | Can articulate the role of each component in the network and how the entire system is dependent on each performing a specific purpose; can rationalise choice of network infrastructure | Understands how decisions around design of networks are affected by multiple factors, and that good designs will incorporate alternative routes for data transmission and redundancy |
| Transmission and structure of data | Identifies that networks allow the transmission of data between computers, and that data carries some meaning | Can explain that data transmission involves more than just the transfer of information and requires metadata to be able to function | Understands the information contained within metadata and can explain how it is used to ensure messages reach their destination | Explains the type of information that is stored in metadata and the limitations this introduces in terms of the rate of transfer and the quantity of message data in each packet |
Draws upon the knowledge they have learned to hypothesise about the nature of data and the challenges inherent in reconstructing it when multiple data streams are being transferred between nodes in a network |
| Network performance | Can identify that different types of physical media change network performance | Can explain the reasons for different physical media performing differently on a network | Can discuss the advantages and disadvantages of using different types of physical media in terms of cost, performance and other factors | Can explain why typical networks use a combination of different types of physical media for communication in terms of cost, convenience and other factors | Can draw conclusions about the choice of physical media in large networks in terms of both intra- and inter-network communications, and factors such as cost, performance, reliability and convenience |
| Network security basics | Understands that modern networks include security features but may not completely understand the need for it | Understands the need for security in networks to ensure data is not altered or intercepted by third parties | Can explain the need for security in networks in terms of data security and privacy, and can provide a simple description of basic techniques used | Understands that network security is achieved through a multi-layered approach, and can explain why more than one layer is necessary for the system to effectively maintain data privacy, security and integrity | Can hypothesise about the value of strong security measures to typical online activities such as banking, identity management and other critical services, and the implications of security breaches on society |
| Approximate grade level | E | D | C | B | A |
While teachers could use aspects of the tasks presented for summative assessment, the following activities and projects are suggested as potential assessment tasks that could be used for evaluation of student learning and generation of grades or scores as required by most jurisdictions and governments.
- Students come up with a new game, or extensions to the CS Unplugged Tablets of Stone activity, that inject additional network infrastructure (for example, routers and firewalls) or security measures (for example, encryption and security certificates), and assess them on correctness and quality of representation.
- Students present their research findings through development of a creative asset (for example, infographic, social media awareness video, podcast episode) that can be published to the wider school community.
- Students use their learning from the activities to write a persuasive letter to their local minister, urging investment in infrastructure to support their future in their industry of interest.
Learning hook
This activity can be made as long or as short as you wish; whilst you can make it a short learning hook, there is potential to revisit this activity as the hook to Computer chatter 2: Network performance.
Transportation networks
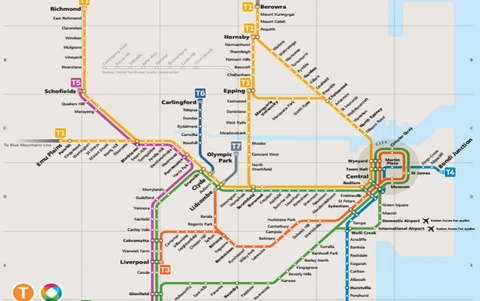
- Provide each student with a copy of a transit network map (for example, the Sydney or London train networks).
In both networks there are multiple ways to get from one station to the other. For this activity, the Sydney network will be used in the examples given. (Here are some useful links: Sydney Train Network, Transport Sydney Trains)
Ideally, localise the context by using a transportation network in your local city, but if you choose to do this make sure the network provides alternative routes to most destinations.
![]()
Additional scaffolding: For students who find this task/concept challenging, you could adapt this task with a map of your school. You could print out a basic map of your school grounds and choose two familiar places that have more than one possible route.
- Give each student a starting point and destination on the network (for example, Liverpool and Chatswood).
It is up to you how many different routes you want to distribute throughout the class, but have about four students working on each route (so, in a class of 24, you would have six different routes shared between the students).
- Have each student individually come up with a route from their starting point to their destination, identifying where they need to stop to change trains, and which lines they are riding on. Once they've got their route worked out, group them up with other students who were doing the same route, and have them share and discuss their solutions.
Have them answer the following questions:
- How many students in your group chose the same route?
- How many different routes were chosen?
- What were the differences between each route? (This might include the number of stops, the number of lines used, the ‘directness’ of the route, etc.)
- Why did each of you choose the route that you did?
- Share some of the students’ answers with the rest of the class through a facilitated discussion. Ask the class if they can see any common patterns emerging about why they chose the routes that they did (for example, did they choose the path with the fewest number of stops?)
- In their groups, have students perform the following tasks on each of the routes the group came up with:
- use the Sydney Trains website to work out how long each of the routes would take to travel
- compare these times with the number of stops on each line and the number of times you need to change trains.
- Have students answer the following questions:
- Is the shortest journey (in terms of number of stops) always the fastest? If not, why might this be the case?
Notes:
- The distances shown on the map are not to scale. The layout of the map is a logical representation of the network rather than an accurate one, so while one way may look shorter than another, it may actually be a longer distance.
- Trains don’t necessarily stop at every station on every journey.
- When you need to change trains, does your journey tend to be longer or shorter
- What other factors haven’t been taken into account that might change the time of your journey?
- When more people are travelling, does it mean they take longer to get on and off at the stations?
- What about the rain? Apparently, umbrellas are a major cause of network delays (see the ‘Rain slows down Sydney trains and buses’ article linked in resources section).
- Is the shortest journey (in terms of number of stops) always the fastest? If not, why might this be the case?
- Finally, ask students (in their groups) how their route might change if one of the following issues arose on the network (choose issues appropriate for each route):
- trains could not stop at any of the ‘city’ stations (marked with the circle on the map)
- the student needs to go via a waypoint to collect something on the way to their destination (for example, they need to meet a friend at Parramatta first)
- trains couldn’t travel through a specific station (for example, Lidcombe)
- one of the lines was out of action (for example, the Green line).
- Can you still get to your destination using trains?
- How has the length of journey been affected?
- What alternatives might there be to overcome the problem?
- Have students share their findings with the rest of the class through facilitated discussion and sharing.
Learning map and outcomes
Once students have shared their findings with the rest of the class, share the learning intentions for the lesson.
For example, in this activity we will:
- learn how networks fit together, and the various components involved
- learn how data is transmitted through networks
- discuss some of the security issues associated with different types of networks.
Learning input
- Explain to students that computer networks work in a similar way to transportation networks:
- just as train networks move people around, computer networks move data around
- just as there are different ways to get from one place to another on a train network, there are often different ways that data can get from one computer to another on a computer network (such as the Internet)
- problems with networks can slow down or prevent data from reaching its destination
- some parts of the network can be more congested than others at different times (just like the city stations), or may be more susceptible to damage or maintenance at particular times.
-
Have students access the HowStuffWorks Tech: How Internet Infrastructure Works resource. (A printable, single-page version of the resource is also available by selecting the ‘Print’ link towards the bottom of the page.) The above example still makes reference to 'dialling in' to the Internet, which is no longer how most people connect. You can use this as an opportunity to talk about how technology has improved over time, and return to this when we explore network performance in the next activity.
![]()
Additional scaffolding: For students who find this task/concept challening, you could first roleplay how messages get from the classroom to the office. You would first relate computer terms to concrete objects:
- IP Address - Name or Number of the Room
- Network - the hallways connecting each room together
- DNS - map of the school
- Node - a person
- Router - the main office
For example, if a student wanted to bring a note (DATA) to the Prinicpal, they would look at the school map (DNS) and likely first go to the office (ROUTER) who would redirect the student to the Principal's office. The Principal could then send a message or document back, minimicing an Internet request.
- Ask them to suggest how the role of each of the following components might be represented in a transportation network:
- home or business network
- ISP network
- router (as an example, this could be an interchange station)
- IP address
- node
- DNS.
There are lots of opportunities to try out some different formative assessment techniques here to gauge the understanding of learners. Try some think, pair, share or one of the other thinking routines found on the formative assessment page.
-
As is always the case with analogies, it is difficult to come up with a perfect mapping between a transportation and computer network, so students may come up with different answers. To determine the ‘correctness’ of the answer, consider whether the student’s answer demonstrates:
- awareness that the Internet is made up of a number of networks linked together
- that different components and technologies on the Internet perform different functions
- the key characteristics of each of the components.
Have them explain the similarities between the component in the computer network and the transportation network, and use this to assess their learning.
Security extension:
- Ask students the following questions:
- How many computers do you have on your network at home?
- What kind of personal data do you have on those computers?
- Do you trust the other computers that you have on your network? Do you trust the people that use them?
- How much of that data would you want other people to be able to access?
- How do you prevent other people from connecting to your network and accessing your data?
Students should very quickly identify that one of the ways we prevent people from accessing the data on our computers is to keep them off our network entirely, and we often do that using some kind of password or other security mechanism.
- Have them think back to the transportation network we've been using in previous activities, and answer the following question:
- What checks does the train network have in place to prevent unauthorised passengers from boarding the trains?
Students should come up with some of the following:
- tickets need to be purchased.
- gates are installed on platforms that don’t let you enter without a ticket.
- ticket inspectors randomly check passenger tickets.
- Ask students the following questions:
- Can you identify any network infrastructure that performs these kinds of activities?
- What applications on your computer check for unwanted data or activity?
Examples of security measures that can protect computer networks include: passwords, security settings on routers, firewalls, security certificates, and anti-virus and anti-malware tools.
Learning construction
- Students will now complete the CS Unplugged Tablets of Stone activity
Note that this activity does not require computer access, and should be done in a large space where students can easily move around.
Some notes about the activity:
- When selecting a message, make it somewhat meaningful – a credit card number or bank account number is best since it will help stimulate student discussion around the importance of it being accurate (and secure if you do the security variation).
- The activity indicates that this can be done with a single messenger, but you’ll find it much more interesting (and quicker) with multiple messengers. For every four pairs you will want one or two messengers, so use this ratio (8:1 or 8:2) to work out how to divide the class up.
- Make sure you have a set of action cards for each messenger, and shuffle them each time you get through the deck so that there is no pattern.
-
Stop the game and discuss the issues mentioned in the activity so that students stay engaged and thinking about the implications of any changes they make to the ‘rules’ of the game.
Some stimulus questions you could use with students include:
- How close do the sent messages look to the received messages?
- If they are different, what could we do to make delivery more reliable?
- Where could information get lost? What about stolen?
-
You can add a security layer to the game if your students are up for it (it generates some interesting discussion and isn't much more complicated). To do this, read the tablets of stone extension and incorporate the suggestions into the rules.
Stimulus questions for the extension might include:
- What causes messages to not be delivered?
- How could you stop the spy from accessing your messages? Changing them?
The addition of the security checks to the game brings it closer to what occurs in real network communication – computers don’t just accept any communication that is addressed to them, and will often have some mechanism in place to check that the content of the message is accurate and safe.
It is also important to reiterate that computers do not have control over all stages of transmission of data, so the message can easily be intercepted by other computers (our messengers) and potentially read or tampered with.What implications do students identify from this? Some students will notice that the ‘security’ measures we have put in place for this activity wouldn't be adequate in the real world; this is a simplified version of the techniques used.
-
At the end of the game, have students record their learning through a quick reflection activity (such as the one described in ‘Learning demo’ below).
Another way of presenting the communication of messages around a network would be to use the analogy of postcards being sent through the mail system. A good explanation of this was presented by Vinton Cerf and can be found here.
- Have students reflect on their learning by writing the thing they found most surprising about the activity on a post-it note and putting it on a ‘reflection wall’ in the classroom.
Learning demo
Whole class activity
Encourage students to share their reflection with others, and to explain why they feel that it is important to understand that aspect of network communication.
Note that the reflection here should focus on the lesson content. Questions that might assist with the reflection could include:
- What was the most challenging part of communicating with a messenger?
- What protocols did you put in place to ensure that messages were transmitted correctly?
- How do you think the transfer of data like this works when you’re watching a video? Downloading a file? Playing an online game?
Learning reflection
Have students complete a Plus, Minus, Interesting (PMI) chart on the activity itself, with the focus this time on the way that other students in the class behaved, or on the activity itself (rather than what was being taught).
For example:
- Plus: ‘Sameera’s suggestion that we wait until we hear that the first message got through before sending a second one was really good’.
- Minus: ‘We didn’t have enough messengers at first, and that meant too much waiting around’.
- Interesting: ‘Adding more messengers without changing the rules didn’t fix the problem – we had to think carefully about why things weren’t working before it was solved’.
Note that the examples don’t talk about the content that was learned, but the process of learning that took place.